what is pegasus spyware 2022?
What is Pegasus? A cybersecurity expert explains how the spyware invades phones and what it does when it gets in
The company's flagship product is Pegasus, spyware that can stealthily enter a smartphone and gain access to everything on it, including its camera and microphone. Pegasus is designed to infiltrate devices running Android, Blackberry, iOS and Symbian operating systems and turn them into surveillance devices.
End-to-end encryption is technology that scrambles messages on your phone and unscrambles them only on the recipients’ phones, which means anyone who intercepts the messages in between can’t read them. Dropbox, Facebook, Google, Microsoft, Twitter and Yahoo are among the companies whose apps and services use end-to-end encryption.
This kind of encryption is good for protecting your privacy, but governments don’t like it because it makes it difficult for them to spy on people, whether tracking criminals and terrorists or, as some governments have been known to do, snooping on dissidents, protesters and journalists. Enter an Israeli technology firm, NSO Group.
The company’s flagship product is Pegasus, spyware that can stealthily enter a smartphone and gain access to everything on it, including its camera and microphone. Pegasus is designed to infiltrate devices running Android, Blackberry, iOS and Symbian operating systems and turn them into surveillance devices. The company says it sells Pegasus only to governments and only for the purposes of tracking criminals and terrorists.
How it works
Earlier version of Pegasus were installed on smartphones through vulnerabilities in commonly used apps or by spear-phishing, which involves tricking a targeted user into clicking a link or opening a document that secretly installs the software. It can also be installed over a wireless transceiver located near a target, or manually if an agent can steal the target’s phone.

Since 2019, Pegasus users have been able to install the software on smartphones with a missed call on WhatsApp, and can even delete the record of the missed call, making it impossible for the the phone’s owner to know anything is amiss. Another way is by simply sending a message to a user’s phone that produces no notification.
This means the latest version of this spyware does not require the smartphone user to do anything. All that is required for a successful spyware attack and installation is having a particular vulnerable app or operating system installed on the device. This is known as a zero-click exploit.
Once installed, Pegasus can theoretically harvest any data from the device and transmit it back to the attacker. It can steal photos and videos, recordings, location records, communications, web searches, passwords, call logs and social media posts. It also has the capability to activate cameras and microphones for real-time surveillance without the permission or knowledge of the user.
Who has been using Pegasus and why
NSO Group says it builds Pegasus solely for governments to use in counterterrorism and law enforcement work. The company markets it as a targeted spying tool to track criminals and terrorists and not for mass surveillance. The company does not disclose its clients.
The earliest reported use of Pegasus was by the Mexican government in 2011 to track notorious drug baron Joaquín “El Chapo” Guzmán. The tool was also reportedly used to track people close to murdered Saudi journalist Jamal Khashoggi.
It is unclear who or what types of people are being targeted and why. However, much of the recent reporting about Pegasus centers around a list of 50,000 phone numbers. The list has been attributed to NSO Group, but the list’s origins are unclear. A statement from Amnesty International in Israel stated that the list contains phone numbers that were marked as “of interest” to NSO’s various clients, though it’s not known if any of the phones associated with numbers have actually been tracked.
A media consortium, the Pegasus Project, analyzed the phone numbers on the list and identified over 1,000 people in over 50 countries. The findings included people who appear to fall outside of the NSO Group’s restriction to investigations of criminal and terrorist activity. These include politicians, government workers, journalists, human rights activists, business executives and Arab royal family members.
Other ways your phone can be tracked
Pegasus is breathtaking in its stealth and its seeming ability to take complete control of someone’s phone, but it’s not the only way people can be spied on through their phones. Some of the ways phones can aid surveillance and undermine privacy include location tracking, eavesdropping, malware and collecting data from sensors.
Governments and phone companies can track a phone’s location by tracking cell signals from cell tower transceivers and cell transceiver simulators like the StingRay device. Wi-Fi and Bluetooth signals can also be used to track phones. In some cases, apps and web browsers can determine a phone’s location.
Eavesdropping on communications is harder to accomplish than tracking, but it is possible in situations in which encryption is weak or lacking. Some types of malware can compromise privacy by accessing data.
The National Security Agency has sought agreements with technology companies under which the companies would give the agency special access into their products via backdoors, and has reportedly built backdoors on its own. The companies say that backdoors defeat the purpose of end-to-end encryption.
The good news is, depending on who you are, you’re unlikely to be targeted by a government wielding Pegasus. The bad news is, that fact alone does not guarantee your privacy.
Pegasus is spyware developed by the Israeli cyber-arms company NSO Group that can be covertly installed on mobile phones (and other devices) running most versions of iOS and Android. Pegasus is able to exploit iOS versions up to 14.6, through a zero-click exploit.
Pegasus aka Q Suite, marketed by the NSO Group aka Q Cyber Technologies as “a world-leading cyber intelligence solution that enables law enforcement and intelligence agencies to remotely and covertly extract” data “from virtually any mobile devices”, was developed by veterans of Israeli intelligence agencies.
Until early 2018, NSO Group clients primarily relied on SMS and WhatsApp messages to trick targets into opening a malicious link, which would lead to infection of their mobile devices. A Pegasus brochure described this as Enhanced Social Engineering Message (ESEM). When a malicious link packaged as ESEM is clicked, the phone is directed to a server that checks the operating system and delivers the suitable remote exploit.
In its October 2019 report, Amnesty International first documented use of ‘network injections’ which enabled attackers to install the spyware “without requiring any interaction by the target”. Pegasus can achieve such zero-click installations in various ways. One over-the-air (OTA) option is to send a push message covertly that makes the target device load the spyware, with the target unaware of the installation over which she anyway has no control.
This, a Pegasus brochure brags, is “NSO uniqueness, which significantly differentiates the Pegasus solution” from any other spyware available in the market.
What kind of devices are vulnerable?
All devices, practically. iPhones have been widely targeted with Pegasus through Apple’s default iMessage app and the Push Notification Service (APNs) protocol upon which it is based. The spyware can impersonate an application downloaded to an iPhone and transmit itself as push notifications via Apple’s servers.
In August 2016, the Citizen Lab, an interdisciplinary laboratory based at the University of Toronto, reported the existence of Pegasus to cyber security firm Lookout, and the two flagged the threat to Apple. In April 2017, Lookout and Google released details on an Android version of Pegasus.
In October 2019, WhatsApp blamed the NSO Group for exploiting a vulnerability in its video-calling feature. “A user would receive what appeared to be a video call, but this was not a normal call. After the phone rang, the attacker secretly transmitted malicious code in an effort to infect the victim’s phone with spyware. The person did not even have to answer the call,” WhatsApp chief Will Cathcart said.
In December 2020, a Citizen Lab report flagged how government operatives used Pegasus to hack 37 phones belonging to journalists, producers, anchors, and executives at Al Jazeera and London-based Al Araby TV during July-August 2020, exploiting a zero-day (a vulnerability unknown to developers) against at least iOS 13.5.1 that could hack Apple’s then-latest iPhone 11. While the attack did not work against iOS 14 and above, the report said the infections it observed were probably a minuscule fraction of the total attacks, given the global spread of the NSO Group’s customer base and the apparent vulnerability of almost all iPhone devices prior to the iOS 14 update.
Does the spyware always get into any device it targets?
Usually, an attacker needs to feed the Pegasus system just the target phone number for a network injection. “The rest is done automatically by the system,” says a Pegasus brochure, and the spyware is installed in most cases.
In some cases, though, network injections may not work. For example, remote installation fails when the target device is not supported by the NSO system, or its operating system is upgraded with new security protections.
 Apparently, one way to dodge Pegasus is to change one’s default phone browser. According to a Pegasus brochure, “installation from browsers other than the device default (and also chrome for android based devices) is not supported by the system”.
Apparently, one way to dodge Pegasus is to change one’s default phone browser. According to a Pegasus brochure, “installation from browsers other than the device default (and also chrome for android based devices) is not supported by the system”.
In all such cases, installation will be aborted and the browser of the target device will display a pre-determined innocuous webpage so that the target does not have an inkling of the failed attempt. Next, an attacker is likely to fall back on ESEM click baits. All else failing, says the brochure, Pegasus can be “manually injected and installed in less than five minutes” if an attacker gets physical access to the target device.
What is Pegasus Spyware and How It Works?
No one can deny that in this digitally advanced era, the incidents of cyberattacks like hacking, data breaches, etc. are increasing exponentially. And in a similar context, recently a term has become very much popular worldwide – ‘Pegasus Spyware’.
If you don’t know about it yet then no worries as here in this article we’re going to know about every crucial aspect of this ‘Pegasus Spyware’ such as what is this, how it works, why it is being used, etc. But before knowing about the ‘Pegasus Spyware’, first, let’s understand what is Spyware? Spyware is some sort of malicious software that is usually installed in your computer or mobile device, even without your consent, to damage your system or steal sensitive data.
What is Pegasus Spyware?
The Pegasus Spyware, created by the Israeli cyber intelligence firm NSO Group, is also designed to hack the computers or mobile devices to gain access to the device and retrieve the data from it without the user’s consent and then deliver it to the third party who is actually spying on you. However, the parent organization of this Pegasus Spyware claims that it is intended to help government authorities to be used against terrorists and criminals by spying on them.
Pegasus Spyware was first identified around 4-5 years ago when a human rights activist from the United Arab Emirates received a text message that was actually a phishing setup. He sent these messages to the security agency and it was found out that if he (the user) had opened those links – his phone would have been infected with the malware, named Pegasus.
Recently, a database of around 50,000 phone numbers that may have been targeted for surveillance using Pegasus, was leaked to several standard investigative media platforms. And most importantly, among these 50,000 contacts, the Pegasus Project (a general name given to this investigative report) found that there are hundreds of public officials contacts also. However, the availability of any number in this database doesn’t compulsorily mean that the respective device was successfully penetrated – and various cyber investigation mechanisms are currently going on for the same.
How Does It work?
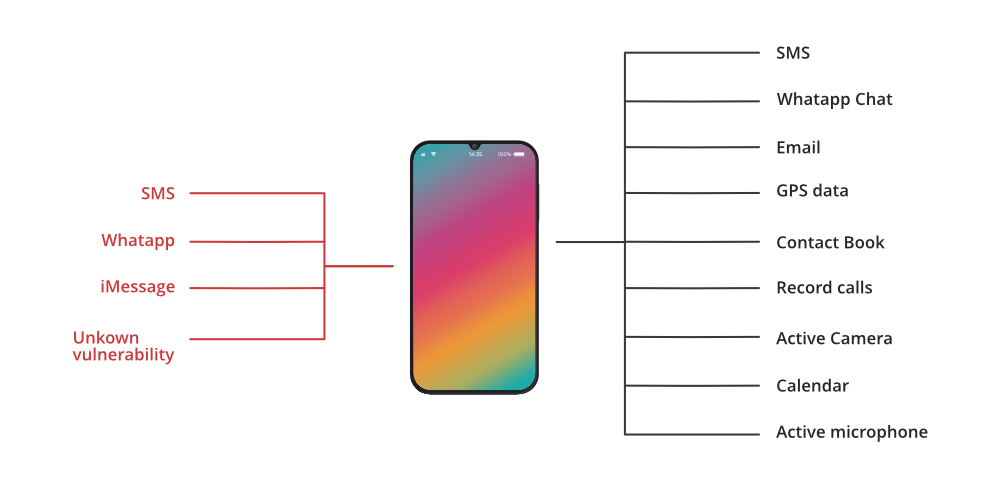
Let us tell you that this Pegasus Spyware attacks the devices so seamlessly that even the device owner might not have any idea about it. You can better understand this with a situation like even a WhatsApp missed call (yes, you heard it right….a missed call) can make the Pegasus Spyware hack your device. Other than that, based on various standard reports, it has been observed that Pegasus is using a variety of endpoints to attack the devices such as it is using iMessage to attack iPhones.
The noticeable thing here is that it follows the zero-click method i.e, the device owner even isn’t required to click on the message, mail, link, etc. or to give any input to make the malware work. On top of that, if the user finds something suspicious and deletes the message – the spyware would still infect the device.
And once the Pegasus gets into your smartphone, now your text messages & emails, contacts, photos, passwords, etc. can be accessed by the other party. In fact, the access is given to such an extent that even your device mic or camera can also be operated by the one who’s is spying on you very conveniently. The Pegasus Spyware can even access the end-to-end encrypted messages or files as it can now steal them before the encryption or after the decryption.
You also need to know that the company behind this Pegasus Spyware made Amazon’s AWS cloud infrastructure as a part of their system – however, now Amazon has deactivated all the accounts of the NSO group after the advent of recent investigation reports.
Can this Pegasus Spyware affect our normal lives? – Okay, firstly we need to understand that as said by NSO Group, the intention behind the development of this ‘Pegasus Spyware’ is to help the government bodies by providing them the advanced technology to detect and prevent terrorism or criminal activities. Also, this spyware is quite expensive to use (as per the reports, it charges government bodies around USD 650,000 to spy on 10 iPhones or android smartphones with some additional charges like installation fee, annual maintenance, etc.) – hence, practically it won’t be feasible for the govt. agencies to use this tool without any solid or justified reason. So, you might consider yourself safe from this Pegasus Spyware due to these particular reasons.
In fact, Apple has also issued a statement over this Pegasus Spyware matter – “Attacks like the ones described are highly sophisticated, cost millions of dollars to develop, often have a short shelf life, and are used to target specific individuals” that is somehow true as well and again depicts that normal users do not need to worry much about it.
But, what if in the future there comes spyware that is as strong (or even more than that) as this Pegasus Spyware and being quite affordable as well – then don’t you think it can be misused and impact normal people lives as well. Yes, that’s actually the point! Instead of just ignoring this Pegasus Spyware, we should be well-aware of this, understand its pros and cons to avoid such kinds of spyware or cyberattacks in the future. For instance, we can consider the below-mentioned points to prevent ourselves from these Spywares likes Pegasus, etc.
- One of the basic approaches is to keep the Operating System and other apps in the device updated.
- Open only those links or messages on your device that are sent by recognized and trusted contacts.
- You should avoid using public WiFi services such as at cafes, parks, etc.
- Always have a backup of the important data stored in your device.
Also, do remember that following the above-mentioned approaches will not make you completely safe from spyware like Pegasus and others – but yes, the more you’ll follow such strategies and preventive measures, the more your risk to get attacked by these Spywares will get reduce!!
End-to-end encryption is technology that scrambles messages on your phone and unscrambles them only on the recipients’ phones, which means anyone who intercepts the messages in between can’t read them. Dropbox, Facebook, Google, Microsoft, Twitter and Yahoo are among the companies whose apps and services use end-to-end encryption.
This kind of encryption is good for protecting your privacy, but governments don’t like it because it makes it difficult for them to spy on people, whether tracking criminals and terrorists or, as some governments have been known to do, snooping on dissidents, protesters and journalists. Enter an Israeli technology firm, NSO Group.
The company’s flagship product is Pegasus, spyware that can stealthily enter a smartphone and gain access to everything on it, including its camera and microphone. Pegasus is designed to infiltrate devices running Android, Blackberry, iOS and Symbian operating systems and turn them into surveillance devices. The company says it sells Pegasus only to governments and only for the purposes of tracking criminals and terrorists.
How it works
Earlier version of Pegasus were installed on smartphones through vulnerabilities in commonly used apps or by spear-phishing, which involves tricking a targeted user into clicking a link or opening a document that secretly installs the software. It can also be installed over a wireless transceiver located near a target, or manually if an agent can steal the target’s phone.

Since 2019, Pegasus users have been able to install the software on smartphones with a missed call on WhatsApp, and can even delete the record of the missed call, making it impossible for the the phone’s owner to know anything is amiss. Another way is by simply sending a message to a user’s phone that produces no notification.
This means the latest version of this spyware does not require the smartphone user to do anything. All that is required for a successful spyware attack and installation is having a particular vulnerable app or operating system installed on the device. This is known as a zero-click exploit.
Once installed, Pegasus can theoretically harvest any data from the device and transmit it back to the attacker. It can steal photos and videos, recordings, location records, communications, web searches, passwords, call logs and social media posts. It also has the capability to activate cameras and microphones for real-time surveillance without the permission or knowledge of the user.
Who has been using Pegasus and why
NSO Group says it builds Pegasus solely for governments to use in counterterrorism and law enforcement work. The company markets it as a targeted spying tool to track criminals and terrorists and not for mass surveillance. The company does not disclose its clients.
The earliest reported use of Pegasus was by the Mexican government in 2011 to track notorious drug baron Joaquín “El Chapo” Guzmán. The tool was also reportedly used to track people close to murdered Saudi journalist Jamal Khashoggi.
It is unclear who or what types of people are being targeted and why. However, much of the recent reporting about Pegasus centers around a list of 50,000 phone numbers. The list has been attributed to NSO Group, but the list’s origins are unclear. A statement from Amnesty International in Israel stated that the list contains phone numbers that were marked as “of interest” to NSO’s various clients, though it’s not known if any of the phones associated with numbers have actually been tracked.
A media consortium, the Pegasus Project, analyzed the phone numbers on the list and identified over 1,000 people in over 50 countries. The findings included people who appear to fall outside of the NSO Group’s restriction to investigations of criminal and terrorist activity. These include politicians, government workers, journalists, human rights activists, business executives and Arab royal family members.
Other ways your phone can be tracked
Pegasus is breathtaking in its stealth and its seeming ability to take complete control of someone’s phone, but it’s not the only way people can be spied on through their phones. Some of the ways phones can aid surveillance and undermine privacy include location tracking, eavesdropping, malware and collecting data from sensors.
Governments and phone companies can track a phone’s location by tracking cell signals from cell tower transceivers and cell transceiver simulators like the StingRay device. Wi-Fi and Bluetooth signals can also be used to track phones. In some cases, apps and web browsers can determine a phone’s location.
Eavesdropping on communications is harder to accomplish than tracking, but it is possible in situations in which encryption is weak or lacking. Some types of malware can compromise privacy by accessing data.
The National Security Agency has sought agreements with technology companies under which the companies would give the agency special access into their products via backdoors, and has reportedly built backdoors on its own. The companies say that backdoors defeat the purpose of end-to-end encryption.
The good news is, depending on who you are, you’re unlikely to be targeted by a government wielding Pegasus. The bad news is, that fact alone does not guarantee your privacy.
Pegasus Spyware and Citizen Surveillance: Here's What You Should Know
For digital spying technology, it's a doozy of a case. Security researchers have revealed evidence of attempted or successful installations of Pegasus, software made by Israel-based cybersecurity company NSO Group, on phones belonging to activists, rights workers, journalists and businesspeople. They appear to have been targets of secret surveillance by software that's intended to help governments pursue criminals and terrorists, and as the months go by, more and more Pegasus infections are emerging.
The most recent revelation is that Pegasus infected the phones of at least 30 Thai activists, according to a July report from Citizen Lab, a Canadian security organization at the University of Toronto. Apple warned those with infected phones in November.
To try to thwart such attacks, Apple has built a new Lockdown Mode into iOS 16, its iPhone software update due to arrive later in 2022, and into its upcoming MacOS Ventura.
The US government is one of the most powerful forces unleashed against Pegasus — even though the CIA and FBI were Pegasus customers, as reported by The New York Times in January. The US Justice Department has launched a criminal investigation, The Guardian said in February, after a whistleblower said NSO Group offered "bags of cash" for sensitive mobile phone data from a US tech firm, Mobileum. The spyware was found on the phones of at least nine State Department officials who were either based in Uganda or involved in matters associated with the African country, Reuters and The New York Times reported in December.
Pegasus is the latest example of how vulnerable we all are to digital prying. Our phones store our most personal information, including photos, text messages and emails. Spyware can reveal directly what's going on in our lives, bypassing the encryption that protects data sent over the internet.
Pegasus has been a politically explosive issue that's put Israel under pressure from activists and from governments worried about misuse of the software. In November, the US federal government took much stronger action, blocking sale of US technology to NSO by putting the company on the government's Entity List. NSO has suspended some countries' Pegasus privileges but has sought to defend its software and the controls it tries to place on its use. NSO Group didn't respond to a request for comment, and the Justice Department declined to comment.
Here's what you need to know about Pegasus.
What is NSO Group?
It's an Israel-based company that licenses surveillance software to government agencies. The company says its Pegasus software provides a valuable service because encryption technology has allowed criminals and terrorists to go "dark." The software runs secretly on smartphones, shedding light on what their owners are doing. Other companies provide similar software.
Hulio co-founded the company in 2010. NSO also offers other tools that locate where a phone is being used, defend against drones and mine law enforcement data to spot patterns.
NSO has been implicated by previous reports and lawsuits in other hacks, including a reported hack of Amazon founder Jeff Bezos in 2018. A Saudi dissident sued the company in 2018 for its alleged role in hacking a device belonging to journalist Jamal Khashoggi, who had been murdered inside the Saudi embassy in Turkey that year.
New Yorker coverage details some of NSO Group's inner workings, including its argument that Pegasus is similar to military equipment that countries routinely sell to other countries, the company's tight ties to the Israeli government and its recent financial difficulties. It also revealed that NSO employees posted on the wall a detailed Google analysis of one Pegasus attack mechanism that concludes its NSO's abilities "rival those previously thought to be accessible to only a handful of nation states."
In the case of the Thai activists, NSO Group didn't comment specifically but told the Washington Post, "Politically motivated organizations continue to make unverifiable claims against NSO."
What is Pegasus?
Pegasus is NSO's best-known product. It can be installed remotely without a surveillance target ever having to open a document or website link, according to The Washington Post. Pegasus reveals all to the NSO customers who control it — text messages, photos, emails, videos, contact lists — and can record phone calls. It can also secretly turn on a phone's microphone and cameras to create new recordings, The Washington Post said.
General security practices like updating your software and using two-factor authentication can help keep mainstream hackers at bay, but protection is really hard when expert, well-funded attackers concentrate their resources on an individual. And Pegasus installations have employed "zero click" attacks that take advantage of vulnerabilities in software like Apple Messages or Meta's WhatsApp to silently install software.
Pegasus isn't supposed to be used to go after activists, journalists and politicians. "NSO Group licenses its products only to government intelligence and law enforcement agencies for the sole purpose of preventing and investigating terror and serious crime," the company says on its website. "Our vetting process goes beyond legal and regulatory requirements to ensure the lawful use of our technology as designed."
Human rights group Amnesty International, however, documents in detail how it traced compromised smartphones to NSO Group. Citizen Lab said it independently validated Amnesty International's conclusions after examining phone backup data and since 2021 has expanded its Pegasus investigations.
In September, though, Apple fixed a security hole that Pegasus exploited for installation on iPhones. Malware often uses collections of such vulnerabilities to gain a foothold on a device and then expand privileges to become more powerful. NSO Group's software also runs on Android phones.
Why is Pegasus in the news?
Forbidden Stories, a Paris journalism nonprofit, and Amnesty International, a human rights group, shared with 17 news organizations a list of more than 50,000 phone numbers for people believed to be of interest to NSO customers.
The news sites confirmed the identities of many of the individuals on the list and infections on their phones. Of data from 67 phones on the list, 37 exhibited signs of Pegasus installation or attempted installation, according to The Washington Post. Of those 37 phones, 34 were Apple iPhones.
The list of 50,000 phone numbers included 10 prime ministers, three presidents and a king, according to an international investigation released in mid-July by The Washington Post and other media outlets, though there's no proof that being on the list means an NSO attack was attempted or successful.
The episode hasn't helped Apple's reputation when it comes to device security. "We take any attack on our users very seriously," Federighi said. The company said it'll donate $10 million and any damages from the lawsuit to organizations that are advocating for privacy and are pursuing research on online surveillance. That's a drop in the bucket for Apple, which reported a profit of $20.5 billion for its most recent quarter, but it can be significant for much smaller organizations, like Citizen Lab.
Whose phones did Pegasus infect?
In April, Citizen Lab also revealed that Pegasus infected the phones of at least 51 people in the Catalonia region of Spain. NSO Group Chief Executive Shalev Hulio told The New Yorker, which covered the hacks in depth, that Spain has procedures to ensure such use is legal, but Citizen Lab said Pegasus attacks targeted the phone of Jordi Solé, a pro-independence member of the European Parliament, digital security researcher Elies Campo and Campo's parents, according to the New Yorker. Catalonia is seeking political independence from Spain, but Spanish police have cracked down on the independence movement.
In addition to Mangin, two journalists at Hungarian investigative outlet Direkt36 had infected phones, The Guardian reported.
A Pegasus attack was launched on the phone of Hanan Elatr, wife of murdered Saudi columnist Jamal Khashoggi, The Washington Post said, though it wasn't clear if the attack succeeded. But the spyware did make it onto the phone of Khashoggi's fiancee, Hatice Cengiz, shortly after his death.
Seven people in India were found with infected phones, including five journalists and one adviser to the opposition party critical of Prime Minister Narendra Modi, The Washington Post said.
And six people working for Palestinian human rights groups had Pegasus-infected phones, Citizen Lab reported in November.
What are the consequences of the Pegasus situation?
The US cut off NSO Group as a customer of US products, a serious move given that the company needs computer processors, phones and developer tools that often come from US companies. NSO "supplied spyware to foreign governments" that used it to maliciously target government officials, journalists, businesspeople, activists, academics and embassy workers. These tools have also enabled foreign governments to conduct transnational repression," the Commerce Department said.
Apple sued NSO Group in November, seeking to bar the company's software from being used on Apple devices, require NSO to locate and delete any private data its app collected, and disclose the profits from the operations. "Private companies developing state-sponsored spyware have become even more dangerous," said Apple software chief Craig Federighi. That suit came after Meta's WhatsApp sued NSO Group in 2019.
French President Emmanuel Macron changed one of his mobile phone numbers and requested new security checks after his number appeared on the list of 50,000 numbers, Politico reported. He convened a national security meeting to discuss the issue. Macron also raised Pegasus concerns with Israeli Prime Minister Naftali Bennett, calling for the country to investigate NSO and Pegasus, The Guardian reported. The Israeli government must approve export licenses for Pegasus.
Israel created a review commission to look into the Pegasus situation. And on July 28, Israeli defense authorities inspected NSO offices in person.
European Commission chief Ursula von der Leyen said if the allegations are verified, that Pegasus use is "completely unacceptable." She added, "Freedom of media, free press is one of the core values of the EU."
The Nationalist Congress Party in India demanded an investigation of Pegasus use.
Edward Snowden, who in 2013 leaked information about US National Security Agency surveillance practices, called for a ban on spyware sales in an interview with The Guardian. He argued that such tools otherwise will soon be used to spy on millions of people. "When we're talking about something like an iPhone, they're all running the same software around the world. So if they find a way to hack one iPhone, they've found a way to hack all of them," Snowden said.
What does NSO have to say about this?
NSO acknowledges its software can be misused. It cut off two customers in recent 12 months because of concerns about human rights abuses, according to The Washington Post. "To date, NSO has rejected over US $300 million in sales opportunities as a result of its human rights review processes," the company said in a June transparency report.
However, NSO strongly challenges any link to the list of phone numbers. "There is no link between the 50,000 numbers to NSO Group or Pegasus," the company said in a statement.
"Every allegation about misuse of the system is concerning me," Hulio told the Post. "It violates the trust that we give customers. We are investigating every allegation."
In a statement, NSO denied "false claims" about Pegasus that it said were "based on misleading interpretation of leaked data." Pegasus "cannot be used to conduct cybersurveillance within the United States," the company added.
Regarding the alleged infection of State Department phones, NSO Group didn't immediately respond to a request for comment. But it told Reuters it canceled relevant accounts, is investigating, and will take legal action if it finds misuse.
NSO will try to reverse the US government's sanction. "We look forward to presenting the full information regarding how we have the world's most rigorous compliance and human rights programs that are based the American values we deeply share, which already resulted in multiple terminations of contacts with government agencies that misused our products," an NSO spokesperson said.
In the past, NSO had also blocked Saudi Arabia, Dubai in the United Arab Emirates and some Mexican government agencies from using the software, The Washington Post reported.
How can I tell if my phone has been infected?
Amnesty International released an open-source utility called MVT (Mobile Verification Toolkit) that's designed to detect traces of Pegasus. The software runs on a personal computer and analyzes data including backup files exported from an iPhone or Android phone


Comments
Post a Comment